In the world of cybersecurity, the tools you choose can make or break your success. For ethical hackers and penetration testers, selecting the right operating system is a critical first step. Kali Linux has long been a household name, but it’s not alone in the race. Parrot Security OS, BlackArch, BackBox, and Pentoo are among the other contenders vying for attention. Each distribution brings unique features and capabilities to the table, tailored to specific needs and skill levels. So, how do you decide which one is right for you? Let’s dive into a detailed comparison to help you make an informed choice.
Kali Linux: The Veteran Leader
For over a decade, Kali Linux has been the go-to operating system for cybersecurity professionals, ethical hackers, and penetration testers. Developed by Offensive Security, Kali Linux remains at the forefront of cybersecurity tools, constantly evolving to address modern challenges in digital security. In 2025, its relevance continues to soar, with new features and updates keeping it indispensable in the rapidly changing world of cybersecurity.

A Brief History of Kali Linux
Kali Linux was introduced in March 2013 as a successor to BackTrack Linux, another security-focused distribution. Built on Debian, Kali Linux offered a more refined, stable, and professional platform for penetration testing. Over the years, its reputation grew as a reliable toolkit for discovering vulnerabilities and testing digital infrastructures.
Why Kali Linux Stands Out
- Comprehensive Toolset: Kali Linux comes preloaded with over 600 penetration testing tools, ranging from network analyzers like Wireshark to exploitation frameworks like Metasploit. This extensive suite makes it a one-stop solution for ethical hackers.
- Community Support: With an active user base and robust documentation, Kali Linux provides excellent support for beginners and seasoned professionals alike. Forums, tutorials, and online courses ensure that users have access to a wealth of resources.
- Customizability: Kali Linux allows users to tailor their environments with custom builds, lightweight versions, and even support for specific hardware like ARM devices.
- Regular Updates: Offensive Security consistently updates Kali Linux, ensuring compatibility with new tools, hardware, and security standards. These updates also address emerging threats in the cybersecurity landscape.
Latest Features of Kali Linux in 2025
As of 2025, Kali Linux has introduced several new features that reinforce its position as the veteran leader in penetration testing:
- Kali Purple: Expanding its focus from offense to defense, Kali Purple provides tools for Blue Team operations, including threat detection, incident response, and system monitoring. This makes Kali Linux a comprehensive platform for both offensive and defensive cybersecurity professionals.
- Dark Mode Enhancement: A refined dark mode interface offers better ergonomics for professionals working long hours.
- AI Integration: With the rise of artificial intelligence in cybersecurity, Kali Linux now includes AI-assisted tools for anomaly detection and vulnerability scanning.
- Improved ARM Support: Enhanced compatibility with Raspberry Pi 5 and other ARM devices ensures Kali Linux remains versatile for mobile and embedded applications.
- Kali NetHunter Pro: The mobile penetration testing platform now features extended support for flagship Android devices, making on-the-go security testing more powerful.
- Cloud Compatibility: Kali Linux’s integration with major cloud platforms such as AWS, Azure, and Google Cloud has been streamlined, enabling seamless cloud penetration testing and cybersecurity assessments.
Learning and Certification
Offensive Security’s certification programs, such as the OSCP (Offensive Security Certified Professional), are heavily tied to Kali Linux. These certifications are highly regarded in the cybersecurity industry and demonstrate proficiency in ethical hacking and penetration testing methodologies.
The Future of Kali Linux
As threats evolve, so will Kali Linux. With an eye on emerging technologies like quantum computing, blockchain security, and IoT vulnerabilities, the development team is poised to keep Kali Linux relevant for years to come. The commitment to open-source principles ensures that Kali Linux remains accessible to all, fostering a global community dedicated to cybersecurity.
Kali Linux is more than just an operating system; it’s a cornerstone of modern cybersecurity practices. Its robust toolset, consistent updates, and adaptability have cemented its status as the veteran leader in penetration testing and ethical hacking. Whether you’re a student, a seasoned professional, or an organization looking to bolster your security posture, Kali Linux continues to be an essential asset in the fight against digital threats.
Parrot Security OS: The Versatile Challenger
Parrot Security OS, commonly known as ParrotOS, is a free and open-source Linux distribution based on Debian, tailored for security experts, developers, and privacy-conscious users. Since its inception in 2013, ParrotOS has evolved into a versatile platform, offering a comprehensive suite of tools for penetration testing, security research, computer forensics, and software development.
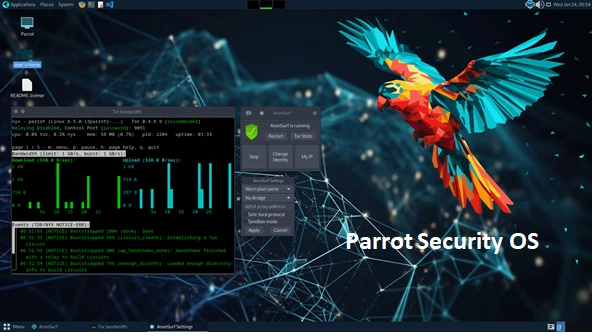
Key Features of Parrot Security OS:
- Comprehensive Toolkit: ParrotOS comes pre-installed with over 600 tools designed for penetration testing, vulnerability assessment, computer forensics, and more, making it a robust platform for cybersecurity professionals.
- Privacy and Anonymity: The operating system includes built-in tools like Tor and AnonSurf to ensure secure and anonymous internet browsing, safeguarding user privacy.
- Resource Efficiency: Designed to be lightweight, ParrotOS can run efficiently on older or low-spec hardware, making it accessible to a broader range of users.
- Regular Updates: ParrotOS is frequently updated to fix bugs and maintain compatibility with the latest security protocols, ensuring a secure and up-to-date environment.
Recent Developments in ParrotOS:
In October 2024, the ParrotOS team released version 6.2, codenamed “Lorikeet.” This update focuses on enhancing performance, increasing stability, and introducing new features to meet the evolving needs of security professionals and developers.
Editions of ParrotOS:
- Home Edition: Designed for daily use, this edition is suitable for regular users seeking a lightweight system for their laptops or workstations. It includes programs for private communication, document encryption, and anonymous browsing.
- Security Edition: Tailored for penetration testing and security assessments, this edition is equipped with a full arsenal of ready-to-use pentest tools, making it ideal for security experts.
- Architect Edition: A minimalist edition that allows users to build a custom system by selecting their preferred software and desktop environment during installation.
- IoT and Cloud Appliances: Special editions designed for embedded devices, cloud environments, virtual machines, and other specialized deployments.
ParrotOS Comparison with Kali Linux:
While both ParrotOS and Kali Linux are popular choices for penetration testing, ParrotOS distinguishes itself with its resource efficiency and user-friendly interface. Its lightweight design makes it suitable for older hardware, and its comprehensive, well-organized documentation appeals to both new and experienced Linux users.
Parrot Security OS stands out as a versatile and powerful operating system, catering to the diverse needs of cybersecurity professionals, developers, and privacy-conscious individuals. Its extensive toolset, commitment to privacy, resource efficiency, and regular updates make it a formidable challenger in the realm of security-focused Linux distributions.
BlackArch Linux: The Toolkit Behemoth
BlackArch Linux is a specialized penetration testing distribution based on Arch Linux, tailored for security researchers and ethical hackers. As of January 2025, it boasts a repository of over 2,800 tools, making it one of the most comprehensive toolkits available for cybersecurity professionals.
BlackArch Linux Overview
Established in 2012, BlackArch has evolved into a robust platform for penetration testing and security analysis. Its rolling release model ensures users have access to the latest tools and updates, maintaining system stability and security. The distribution supports multiple architectures, including x86-64 and aarch64, broadening its applicability across various hardware platforms.
BlackArch Linux Toolset
The extensive collection of tools in BlackArch is organized into categories, facilitating easy navigation and selection based on specific security testing needs. These categories encompass:
- Anti-Forensic
- Automation
- Backdoor
- Cracker
- Crypto
- Forensic
- Networking
- Scanner
- Wireless
This categorization enables users to efficiently locate tools pertinent to their tasks.
BlackArch Linux Installation and Usage
BlackArch can be utilized in several ways:
- Live ISO: Allows users to boot directly into BlackArch without installation, providing a portable penetration testing environment.
- Full Installation: For users seeking a dedicated system, BlackArch can be installed as the primary operating system, offering a comprehensive suite of tools out-of-the-box.
- As an Unofficial User Repository: Existing Arch Linux users can integrate BlackArch’s repository into their systems, enabling the installation of individual tools as needed without overhauling their current setup.
This flexibility caters to a wide range of user preferences and requirements.
Community and Development
The development of BlackArch is driven by a dedicated team of cybersecurity specialists and researchers who continuously add new tools and ensure compatibility with the latest Arch Linux updates. The project’s open-source nature encourages community involvement, allowing users to contribute to its growth and improvement.
BlackArch Linux stands as a formidable toolkit for penetration testers and security researchers, offering an expansive array of tools within a flexible and user-friendly environment. Its commitment to providing up-to-date resources and its integration capabilities with existing Arch Linux systems make it a valuable asset in the field of cybersecurity.
For a visual overview and further insights into BlackArch, you might find the following video helpful:
BackBox Linux: The User-Friendly Underdog
BackBox is an Ubuntu-based Linux distribution tailored for penetration testing and security assessments. It offers a comprehensive suite of tools for ethical hacking, making it a formidable contender in the cybersecurity domain.
Latest Release: BackBox Linux 9
As of October 30, 2024, BackBox Linux 9 is the latest version, introducing several enhancements:
- Updated Tools: Integration of the latest versions of essential security tools, ensuring users have access to current features and capabilities.
- Performance Improvements: Optimizations for better system performance and resource management.
- Enhanced User Interface: Refinements to the XFCE desktop environment for a more intuitive user experience.
BackBox Linux Key Features
- Comprehensive Toolkit: BackBox includes a wide array of tools for various security-related tasks, such as:
- Information Gathering: Nmap, Wireshark
- Vulnerability Assessment: OpenVAS
- Exploitation: Metasploit
- Privilege Escalation: John The Ripper
- Maintaining Access: The Social Engineering Toolkit
- Documentation & Reporting: Various tools to aid in reporting findings
- Lightweight Environment: Utilizing the XFCE desktop environment, BackBox ensures a balance between performance and functionality, making it suitable for systems with varying resource capacities.
- Regular Updates: The BackBox team is committed to providing regular updates, integrating the latest security tools and patches to keep the distribution current.
Community and Support
BackBox boasts an active community that contributes to its development and provides support to users. This collaborative environment fosters continuous improvement and knowledge sharing among cybersecurity professionals and enthusiasts.
BackBox stands out as a user-friendly yet powerful Linux distribution for security professionals. Its comprehensive toolset, combined with a commitment to regular updates and community engagement, solidifies its position as a valuable resource in the cybersecurity field.
Pentoo Linux: For Power Users
Pentoo is a specialized Linux distribution tailored for penetration testing and security assessments. Built on the Gentoo Linux framework, it offers a high degree of customization, making it a preferred choice for power users and security professionals.
Key Features of Pentoo:
- Gentoo Foundation: Pentoo inherits Gentoo’s source-based approach, allowing users to compile software packages with specific optimizations. This ensures that applications are fine-tuned for the user’s hardware and requirements.
- Security Tools Integration: Pentoo comes preloaded with a comprehensive suite of tools categorized for various security tasks, including analyzers, wireless testing, database assessment, and man-in-the-middle attacks. This extensive toolkit supports professionals in conducting thorough security evaluations.
- Hardened Kernel: The distribution features a hardened Linux kernel with grsecurity and PAX patches, enhancing system security by providing additional memory protections and mitigating potential vulnerabilities.
- GPU Acceleration: Pentoo includes support for GPGPU (General-Purpose computing on Graphics Processing Units) cracking software, enabling users to leverage OpenCL and CUDA technologies for accelerated password recovery and cryptographic analysis.
- Live Environment: Available as both a Live CD and Live USB, Pentoo allows users to boot directly into a fully functional environment without installation. This feature is particularly useful for on-the-go security assessments and testing.
Recent Developments:
As of January 2024, Pentoo released version 2024.0, continuing its commitment to providing up-to-date tools and features for security professionals. The development team maintains an active presence, ensuring regular updates and improvements to the distribution.
Considerations for Power Users:
While Pentoo offers extensive customization and a rich set of tools, it requires a certain level of expertise to fully utilize its capabilities. The source-based nature of Gentoo means that software installations involve compiling packages, which can be time-consuming and may present challenges for users unfamiliar with this process.
Pentoo stands out as a robust and flexible platform for security professionals seeking a customizable environment tailored to penetration testing and security analysis. Its integration of advanced tools, hardened security features, and the flexibility inherited from Gentoo makes it a powerful choice for users who demand control and precision in their security endeavors.
How to Choose the Right Penetration Testing Distributions
- Skill Level: If you’re new to penetration testing, Kali Linux or BackBox is a great starting point. Advanced users may prefer BlackArch or Pentoo for their extensive toolsets and customizability.
- System Resources: For older or less powerful hardware, consider lightweight options like Parrot Security OS or BackBox.
- Privacy Needs: Parrot Security OS stands out for its built-in anonymity tools, making it ideal for users prioritizing privacy.
- Specific Use Cases: If your work requires niche tools, BlackArch’s extensive library is unbeatable. For general-purpose penetration testing, Kali Linux remains the go-to.
Comparison Table Kali Linux Vs. Competing Penetration Testing Distributions
| Distribution | Key Features | Pros | Cons |
|---|---|---|---|
| Kali Linux | Veteran with 600+ pre-installed tools | Comprehensive toolset- Broad community support- Regular updates- Customizability | Resource-intensive- Not privacy-focused |
| Parrot Security | Lightweight and privacy-focused OS | Runs on older hardware- Built-in privacy tools- Versatile for multiple uses- Rolling updates | Smaller toolset compared to Kali- Less extensive community support |
| BlackArch Linux | Extensive toolset with 3,000+ tools | Largest tool library- Benefits from Arch Linux base- Granular control for advanced users | Steep learning curve- Resource-heavy |
| BackBox Linux | Ubuntu-based, beginner-friendly | Intuitive interface- Lightweight- Focuses on essential tools | Limited toolset- Smaller ecosystem |
| Pentoo Linux | Gentoo-based for power users | – Deep customization- Kernel enhancements- Efficient package management | Requires advanced knowledge- Niche community support |
Conclusion
Choosing the right penetration testing distribution is all about aligning your needs with the strengths of each option. Kali Linux is the go-to choice for its comprehensive toolset and ease of use, making it a favorite among professionals and beginners alike. However, if you prioritize lightweight performance and privacy, Parrot Security OS offers an excellent alternative. For power users who demand customization and an expansive toolkit, BlackArch or Pentoo might be your best bet. BackBox, with its user-friendly interface, is perfect for newcomers seeking simplicity.
Remember, the best way to find your ideal match is by experimenting with multiple distributions. Your journey in cybersecurity will be as unique as the tools you choose—so don’t hesitate to explore and adapt to what suits your workflow best!
Disclaimer
The information provided in this article is for educational purposes only. The use of penetration testing tools and distributions should always comply with local laws and ethical guidelines. Unauthorized or malicious use of these tools is illegal and can result in severe penalties. Always obtain proper authorization before conducting any security testing.
Also Read
Mastering Fedora 41: Installation, Setup, and Tips for New Users


