
Top 5 Privacy-Focused Operating Systems for Secure Browsing in 2025
Imagine a world where your every click, search, and keystroke isn’t being watched, tracked, or logged. Sounds like a dream, right? In today’s hyper-connected age, maintaining online privacy feels like swimming against a tide of surveillance and data breaches. But what if the very foundation of your digital life—your operating system—could be your strongest ally in protecting your privacy?
Privacy-focused operating systems are the unsung heroes of the tech world. Built with security and anonymity at their core, they provide a safe haven from prying eyes, empowering you to browse, work, and communicate without compromise. Whether you’re a privacy enthusiast, a journalist safeguarding sensitive information, or just someone tired of being tracked, there’s an OS tailored for you.
So, let’s uncover the top five operating systems that redefine online privacy and give you the ultimate power to take control of your digital footprint.
Top 5 Privacy-Focused Operating Systems for Secure Browsing in 2025
1. Tails (The Amnesic Incognito Live System)
In a world where online privacy is constantly under threat, Tails (The Amnesic Incognito Live System) stands as a beacon of hope for those who value anonymity and security. Designed as a portable operating system, Tails can be used on almost any computer without leaving a trace. Let’s dive into what makes Tails unique and why it’s a vital tool for journalists, activists, and privacy-conscious individuals.
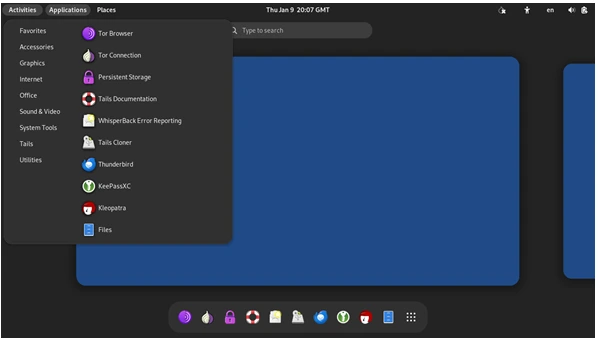
What is Tails?
Tails is a Debian-based Linux distribution that prioritizes privacy and anonymity. It runs entirely from a USB stick or DVD, meaning it doesn’t interfere with your computer’s existing operating system. Once you remove the USB or DVD and shut down the computer, Tails erases all traces of your activity, leaving no footprint behind.
The operating system forces all internet traffic through the Tor network, a globally distributed network that anonymizes your connection by routing it through multiple nodes. This ensures that your online activities are untraceable and secure.
Key Features of Tails
1. Anonymity by Default
- Every application in Tails is configured to use the Tor network. This includes the web browser, email client, and instant messaging apps.
- Your real IP address is hidden, and tracking attempts by websites are thwarted.
2. Amnesic Nature
Tails doesn’t store any data on the computer it’s used on. When you power off, all session data disappears unless you explicitly save it in an encrypted persistent storage.
3. Pre-installed Privacy Tools
- Tails comes with tools like the Tor Browser, OnionShare for secure file sharing, and GnuPG for encrypted communication.
- VeraCrypt is also included for creating and accessing encrypted volumes.
4. Built-in Security
- Tails includes an application firewall that blocks all non-anonymous connections.
- Regular updates ensure protection against vulnerabilities and exploits.
5. Easy to Use
Despite its focus on privacy, Tails is designed to be user-friendly. The interface is straightforward, and the documentation is comprehensive, making it accessible even to non-technical users.
Who Uses Tails?
Tails is often the operating system of choice for:
- Journalists: Protecting their sources and communicating securely.
- Activists: Operating in restrictive regimes where anonymity is critical.
- Whistleblowers: Ensuring their identity remains concealed while exposing wrongdoing.
- Everyday Users: Anyone who values privacy and wants to minimize digital footprints.
Setting Up Tails
1. Download Tails
- Visit the official Tails website and download the ISO file.
2. Create a Bootable USB/DVD
- Use tools like Rufus (for Windows) or Etcher (for Linux/Mac) to create a bootable USB.
3. Boot into Tails
- Plug the USB or insert the DVD into your computer. Restart the system and boot from the USB/DVD. Follow the on-screen instructions to start using Tails.
4. (Optional) Configure Persistent Storage
- If you need to save data (e.g., documents, browser bookmarks), you can set up encrypted persistent storage on your USB stick.
Limitations of Tails
While Tails is powerful, it’s not without its limitations:
- Hardware Compatibility: Some computers may not boot from Tails due to BIOS/UEFI restrictions.
- Internet Speed: Using Tor can slow down your connection.
- Learning Curve: Understanding Tor and privacy practices might require some initial effort.
- No Complete Anonymity: Tails provides strong privacy, but user errors (e.g., logging into personal accounts) can still compromise anonymity.
Why Tails Matters
In an age where digital surveillance is pervasive, Tails provides a lifeline for those who need to protect their identity and communications. Whether you’re escaping censorship, sharing sensitive information, or simply browsing privately, Tails empowers you to reclaim your online freedom.
By leveraging tools like Tails, you’re not just protecting yourself; you’re contributing to a world where privacy is a fundamental right, not a privilege.
Have you tried Tails? Share your experiences or questions in the comments below!
2. Qubes OS: The Fortress of Security for Your Digital Life
In a world where data breaches and cyber threats are becoming more sophisticated every day, protecting your personal and professional information is no longer optional. Enter Qubes OS, a security-focused operating system that offers an innovative approach to digital protection. Unlike traditional operating systems, Qubes OS is built with the idea of “security by compartmentalization” at its core, making it a favorite among privacy enthusiasts, developers, and even whistleblowers.

What Is Qubes OS?
Qubes OS is an open-source operating system designed to provide robust security through isolation. Instead of running all your applications and processes in a single environment, Qubes OS separates them into virtual machines (VMs), called “qubes.” Each qube is isolated from the others, so even if one gets compromised, the rest of your system remains secure. Think of it as having a separate, locked room for each of your activities within a single house.
Built on top of Xen virtualization technology, Qubes OS is compatible with a wide range of hardware, though it does have specific requirements for optimal performance. Its unique architecture ensures that your sensitive tasks—like online banking, work-related activities, or personal browsing—are kept separate and secure.
How Qubes OS Works
The core philosophy of Qubes OS revolves around compartmentalization. Here’s how it works:
1. Virtualized Workspaces: Every task or application runs in its own isolated virtual machine. For instance, you can have one VM for work, another for personal browsing, and yet another for handling sensitive documents. These VMs are visually represented with colored borders, making it easy to distinguish between them.
2. Minimal Attack Surface: By isolating tasks, Qubes OS minimizes the attack surface. Even if malware infects one VM, it cannot affect others or access the underlying system.
3. Template-Based Management: Qubes OS uses templates to manage software installations. Instead of installing applications in each VM, you can install them in a template that multiple VMs can share. This approach saves resources and simplifies updates.
4. Seamless Integration: Despite the isolation, Qubes OS offers a seamless user experience. Files can be securely transferred between VMs, and you can copy and paste text while maintaining security.
Who Should Use Qubes OS?
While anyone can benefit from the enhanced security of Qubes OS, it’s particularly well-suited for:
- Privacy Advocates: If you’re concerned about surveillance or data tracking, Qubes OS offers a secure environment to safeguard your information.
- Developers and IT Professionals: Its ability to isolate testing environments and run multiple operating systems side by side makes it a powerful tool for tech enthusiasts.
- Journalists and Whistleblowers: With its robust security measures, Qubes OS is ideal for those handling sensitive information or communicating with confidential sources.
Getting Started with Qubes OS
Here’s what you need to know before diving in:
1. System Requirements: Qubes OS has specific hardware requirements, such as a 64-bit Intel or AMD processor with virtualization support, at least 16GB of RAM, and an SSD for optimal performance. Check the official hardware compatibility list for details.
2. Installation: Download the ISO file from the official Qubes OS website, create a bootable USB drive, and follow the installation instructions. The process is straightforward but requires some technical know-how.
3. Learning Curve: Qubes OS isn’t as user-friendly as mainstream operating systems like Windows or macOS. However, its comprehensive documentation and active community make it easier to get up to speed.
Pros and Cons of Qubes OS
Pros:
- Exceptional security through compartmentalization
- Open-source and free to use
- Highly customizable for advanced users
- Compatible with multiple operating systems (Windows, Linux, etc.) within VMs
Cons:
- Steep learning curve for beginners
- Requires high-end hardware for smooth operation
- Not ideal for gaming or resource-intensive applications
Why Qubes OS Matters
In an era where digital security is paramount, Qubes OS stands out as a pioneer in delivering practical, effective solutions to combat cyber threats. By isolating tasks and reducing the impact of potential vulnerabilities, it offers a level of protection that traditional operating systems simply can’t match.
If you’re serious about securing your digital life, Qubes OS is worth exploring. While it may take some time to adapt to its unique approach, the peace of mind it provides is well worth the effort.
So, are you ready to take control of your digital security? With Qubes OS, you can transform your computer into a fortress and safeguard your most valuable asset—your data.
3. Exploring Linux Kodachi: The Ultimate Secure OS for Privacy Enthusiasts
In today’s world, where digital privacy is under constant threat, having a secure and private operating system is more important than ever. Enter Linux Kodachi – a lightweight, privacy-focused Linux distribution designed to protect your online anonymity and secure your sensitive data. Whether you’re a journalist working under strict confidentiality, a whistleblower, or simply someone who values their online privacy, Linux Kodachi has something to offer.
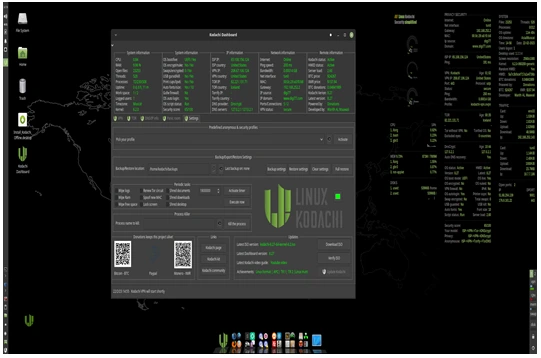
What is Linux Kodachi?
Linux Kodachi is a Debian-based operating system specifically tailored for users who prioritize privacy, security, and anonymity. It is designed to be run as a live operating system, meaning you can boot it directly from a USB stick or DVD without installing it on your hard drive. This approach ensures that no traces of your activity are left on the host system once you’re done.
Developed with privacy in mind, Kodachi comes preloaded with tools and configurations that make it easier for users to stay anonymous online. It routes all internet traffic through a VPN, followed by the Tor network, and finally through a DNSCrypt-protected server, providing multiple layers of encryption and masking your IP address.
Key Features of Linux Kodachi
1. Built-in VPN and Tor Support
Linux Kodachi automatically connects to a VPN upon booting up. After the VPN, it directs all traffic through the Tor network, making your online activity nearly impossible to trace. If you’re already using a VPN service, you can configure Kodachi to use your credentials.
2. DNSCrypt Protection
DNSCrypt ensures that your DNS queries are encrypted, preventing any potential DNS-based attacks or surveillance. This adds an extra layer of security to your internet usage.
3. Secure Wipe and RAM Cleanup
Kodachi includes tools to securely erase data from storage devices and cleanse RAM to eliminate any traces of your activity. These features are especially useful when using shared or public systems.
4. Pre-installed Privacy Tools
Kodachi comes with a host of pre-installed privacy tools, including:
- VeraCrypt for disk encryption.
- Electrum Bitcoin Wallet for cryptocurrency transactions.
- OnionShare for anonymous file sharing.
- KeePassXC for password management.
5. Amnesic Nature
Since Kodachi is primarily designed to run as a live OS, it doesn’t write data to the host system’s hard drive by default. Once you shut down Kodachi, all your activities and traces disappear, ensuring no data is left behind.
6. Resource-Friendly
Despite being packed with features, Kodachi is lightweight and runs smoothly even on older hardware. Its XFCE desktop environment ensures a user-friendly and customizable experience.
Why Choose Linux Kodachi?
Unlike many other privacy-focused operating systems, Kodachi offers a balance between usability and advanced security. You don’t need to be a tech wizard to use it; everything is pre-configured to work right out of the box. For those who want more control, Kodachi also allows manual customization of its security and privacy features.
Moreover, Kodachi’s focus on multi-layered security (VPN + Tor + DNSCrypt) makes it a standout choice for users who need robust protection against surveillance and cyberattacks. Whether you’re accessing sensitive information, engaging in confidential communication, or simply browsing the web, Kodachi provides peace of mind.
Getting Started with Linux Kodachi
1. Download the ISO
Head over to the official Linux Kodachi website to download the latest ISO file.
2. Create a Bootable USB or DVD
Use tools like Rufus (for Windows) or Etcher (for Linux/Mac) to create a bootable USB or DVD.
3. Boot into Kodachi
Insert your bootable device into your computer and boot into Kodachi. You may need to change the boot order in your system’s BIOS/UEFI settings.
4. Explore the Features
Once the system is up and running, you’ll find a clean and intuitive desktop environment. Explore the pre-installed tools and adjust the settings to suit your needs.
In an era where online privacy is increasingly compromised, Linux Kodachi emerges as a powerful ally. Its seamless integration of privacy tools, multi-layered encryption, and user-friendly interface make it an excellent choice for anyone serious about staying secure online.
Whether you’re an activist, journalist, or just someone who values their digital footprint, Linux Kodachi is worth considering. Give it a try, and experience a new level of online privacy and security.
4. Whonix: Your Ultimate Gateway to Online Privacy and Anonymity
In a world where digital privacy is becoming a rare commodity, tools like Whonix are stepping up to safeguard our online activities. But what exactly is Whonix, and why should you consider using it? Let’s break it down in simple terms.
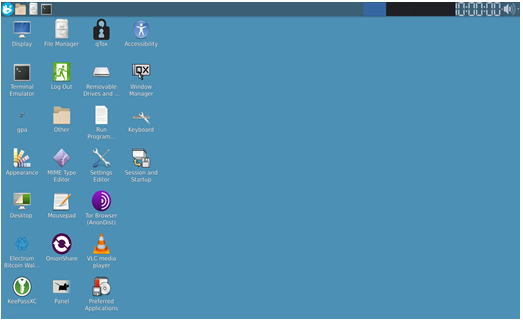
What is Whonix?
Whonix is a Linux-based operating system designed with one primary goal: to provide unparalleled anonymity and security while you browse the internet. Built on the principles of isolation and Tor-based anonymity, Whonix ensures that your identity and online activities remain hidden from prying eyes.
What sets Whonix apart from other privacy tools is its architecture. It operates using two virtual machines (VMs):
1. Whonix-Gateway: This VM routes all internet traffic through the Tor network, masking your IP address and encrypting your data.
2. Whonix-Workstation: This VM is isolated and uses the Whonix-Gateway for all its internet connectivity. This design ensures that even if the Workstation is compromised, your real IP and identity remain secure.
Key Features of Whonix
1. Tor Integration: Whonix leverages the Tor network to anonymize your traffic, making it nearly impossible for third parties to trace your online activities.
2. Isolation for Security: The separation between Gateway and Workstation VMs ensures that vulnerabilities in one don’t affect the other.
3. Protection Against Malware: Even if your Workstation VM is attacked, Whonix’s design prevents the attacker from discovering your real IP address.
4. Open Source: Whonix’s code is openly available for review, ensuring transparency and trustworthiness.
Why Should You Use Whonix?
Here are a few reasons why Whonix is worth considering:
1. Journalists and Activists: If you’re in a country with strict censorship or surveillance laws, Whonix provides a safe way to communicate and share information.
2. Researchers: For those investigating sensitive topics, Whonix offers a shield against online tracking and potential threats.
3. Everyday Users: Even if you’re not handling sensitive information, protecting your privacy is always a good idea in today’s digital age.
How to Get Started with Whonix
Getting started with Whonix is easier than you might think. Here’s a quick guide:
1. Download VirtualBox: Whonix runs as a set of virtual machines, so you’ll need VirtualBox or KVM (another virtualization tool) installed on your system.
2. Download Whonix: Head over to the official Whonix website and download the Whonix-Gateway and Whonix-Workstation VMs.
3. Import VMs: Import the downloaded VMs into VirtualBox and configure them as per the instructions provided on the website.
4. Run Whonix: Start the Gateway VM first, followed by the Workstation VM. You’re now ready to browse the web with enhanced anonymity.
Tips for Using Whonix Effectively
1. Avoid Personal Information: Don’t log into accounts or share information that can reveal your identity.
2. Use Encrypted Communication: Combine Whonix with encrypted email services or messengers for added security.
3. Stay Updated: Regularly update Whonix to benefit from the latest security patches and features.
The Bottom Line
In an era where privacy is under constant threat, Whonix stands out as a robust solution for anyone seeking true anonymity online. Whether you’re a journalist, researcher, or just someone who values their privacy, Whonix offers a simple yet powerful way to protect your digital footprint.
Give Whonix a try, and take the first step towards reclaiming your online privacy today.
5. PureOS: A Privacy-Focused Operating System for the Conscious Tech User
In the ever-evolving world of technology, the debate over privacy, security, and open-source software continues to gain momentum. If you’re someone who values these principles, you may have come across PureOS. But what exactly is it, and why is it worth your attention? Let’s dive into what makes PureOS a standout operating system in the realm of Linux-based distributions.

What is PureOS?
PureOS is a free and open-source GNU/Linux distribution developed by Purism, a company known for its privacy-focused devices like the Librem laptops and Librem 5 smartphone. Designed with security and user privacy at its core, PureOS is based on Debian but stands apart by offering a completely free software ecosystem. That’s right—no proprietary drivers or software here.
The system has been endorsed by the Free Software Foundation (FSF), a badge of honor that guarantees its adherence to free software principles. It’s an operating system designed for people who prioritize transparency and control over their digital lives.
Privacy First: What Makes PureOS Unique?
1. Default Security Features
PureOS comes preloaded with privacy-focused tools. HTTPS Everywhere, Privacy Badger, and the DuckDuckGo search engine are part of its default setup. For browsing, it includes the Tor Browser, which offers anonymity by routing your traffic through a network of servers.
2. Freedom from Surveillance
Unlike many operating systems that rely on proprietary software, PureOS is built entirely on free and open-source code. This ensures there’s no hidden surveillance or tracking, making it a great choice for privacy advocates.
3. App Ecosystem Focused on Privacy
The PureOS Store curates apps that align with privacy principles. From encrypted email clients like Thunderbird to office tools such as LibreOffice, every app is chosen with security and open-source philosophy in mind.
Performance and Usability
One might think that focusing on privacy could compromise user experience, but that’s not the case with PureOS. The OS uses GNOME as its default desktop environment, offering a modern and intuitive user interface. Whether you’re a tech-savvy developer or a Linux newbie, the user-friendly design makes navigation seamless.
Performance-wise, PureOS holds its ground. It’s lightweight, ensuring smooth operation even on older hardware. Whether you’re multitasking with apps or browsing heavily encrypted websites, PureOS keeps up without a hitch.
Who Should Use PureOS?
PureOS isn’t for everyone—and that’s okay. It’s not aimed at gamers or people heavily reliant on proprietary software like Adobe Creative Suite or Microsoft Office. Instead, it’s ideal for:
- Privacy Advocates: If privacy is your top concern, PureOS is a perfect fit.
- Open-Source Enthusiasts: Those who believe in free software and the principles of transparency will appreciate PureOS’s dedication.
- Everyday Users: Even if you’re not tech-savvy, PureOS is easy to set up and use. Its default configuration is perfect for general browsing, email, and productivity.
Downsides to Consider
Like every operating system, PureOS has its drawbacks:
- Limited Software Compatibility: Proprietary software that relies on non-free drivers won’t run.
- Gaming Restrictions: PureOS isn’t optimized for gaming, as most popular gaming platforms like Steam require proprietary software.
- Learning Curve: For those accustomed to Windows or macOS, transitioning to PureOS might take some time.
PureOS is more than just another Linux distro—it’s a philosophy in action. With privacy and security baked into its DNA, it offers a robust alternative to mainstream operating systems. Whether you’re looking for a daily driver or an OS for specific privacy-conscious tasks, PureOS is worth considering.
In an age where data breaches and surveillance are the norm, PureOS serves as a reminder that technology doesn’t have to compromise ethics. If you’re ready to take control of your digital life, PureOS might just be the operating system you’ve been looking for.
Have you tried PureOS? Share your experience in the comments!
System Requirements Table for Privacy-Focused Operating Systems
| Operating System | Minimum RAM | Minimum Storage | Processor Requirements | Additional Notes |
|---|---|---|---|---|
| Tails | 2 GB | 8 GB USB Stick | 64-bit x86 processor | Requires bootable USB or DVD. |
| Qubes OS | 4 GB (8 GB recommended) | 32 GB (minimum) | 64-bit Intel/AMD processor with VT-x/AMD-V and SLAT (e.g., EPT) support | High-performance hardware recommended. |
| Linux Kodachi | 2 GB | 20 GB | 64-bit x86 processor | Built-in VPN and Tor for enhanced security. |
| Whonix | 4 GB | 20 GB | 64-bit x86 processor | Requires virtualization software like VirtualBox. |
| PureOS | 2 GB | 25 GB | 64-bit processor | Designed for user-friendliness and everyday use. |
Final Thoughts
Selecting a privacy-focused operating system depends on your specific needs and technical proficiency. If you’re looking for maximum anonymity, Tails or Whonix might be your best bet. For those who value security through isolation, Qubes OS is unparalleled. Meanwhile, Linux Kodachi and PureOS offer more user-friendly options for secure browsing.
By choosing any of these operating systems, you’re taking a significant step toward protecting your digital privacy. Remember, however, that no OS can guarantee 100% security. Complement your choice with good digital hygiene—use strong passwords, keep your software updated, and stay vigilant against phishing attacks.
Disclaimer:
This article is intended for informational purposes only. While privacy-focused operating systems can enhance your digital security and anonymity, no solution guarantees 100% protection against all threats. Users should exercise additional caution, adopt safe browsing practices, and stay informed about emerging cybersecurity risks. Always research and choose the tools that best suit your personal needs and technical expertise.
What’s your favorite privacy-focused OS? Let us know in the comments below!
Also Read,
Eye Candy for Your Desktop: 5 Most Beautiful Linux Distributions of 2025




